You can add the following in the ansible config file in “inventory/host_vars/matrix.yourdomain.com/vars.yml” to use a self signed certificate. Only recommended for testing purposes.
matrix_ssl_retrieval_method: self-signed

You can add the following in the ansible config file in “inventory/host_vars/matrix.yourdomain.com/vars.yml” to use a self signed certificate. Only recommended for testing purposes.
matrix_ssl_retrieval_method: self-signed
ansible-playbook -i inventory/hosts setup.yml --tags=setup-system-user --ask-become-pass
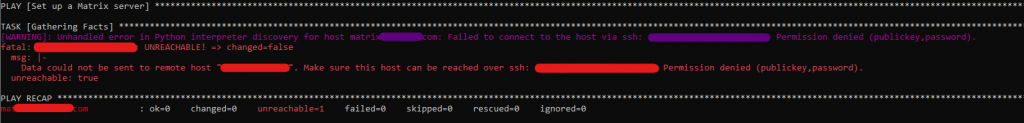
Looks like the above issue is that Ansible is not able to authenticate with the server. By default it looks to try and use ssh keys, but I don’t have any passwordless ssh keys set up for Ansible to use so it fails while attempting to connect. The work around it to make sure you have sshpass installed and then specify –ask-pass to the end of the command.
ansible-playbook -i inventory/hosts setup.yml --tags=setup-system-user --ask-become-pass --ask-pass
When the command runs it’ll ask you for the ssh password and then use that.
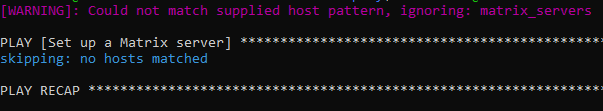
If you get the above error when you try running
ansible-playbook -i inventory/hosts setup.yml --tags=setup-system-user
Check and verify that you have [matrix_servers] in your inventory/hosts file
That file should contain the following.
[matrix_servers] matrix. ansible_host= ansible_ssh_user=root
This is part of a series of posts on backing up and restoring a backup for Matrix Synapse server. Synapse was installed using the matrix-docker-ansible deployment which while a little complicated can greatly ease management later on down the road. All the main components are in docker containers so we need to use docker to access.
As the root user run
docker exec --env-file=/matrix/postgres/env-postgres-psql matrix-postgres pg_dumpall -h matrix-postgres | gzip -c > /matrix/postgres.sql.gz
This will dump the Postgres database in /matrix/postgres.sql.gz
We can use this later to restore to a new server or keep as a backup.