SSH into radio
ssh ubnt@192.168.1.20
Put the following two lines into the /tmp/system.cfg file. Doesn’t matter where
unms.uri=REPLACE-WITH-UNMS-KEY unms.status=enabled
Apply changes with
/usr/etc/rc.d/rc.softrestart save
Go accept device in UNMS.

SSH into radio
ssh ubnt@192.168.1.20
Put the following two lines into the /tmp/system.cfg file. Doesn’t matter where
unms.uri=REPLACE-WITH-UNMS-KEY unms.status=enabled
Apply changes with
/usr/etc/rc.d/rc.softrestart save
Go accept device in UNMS.
The following is a method to recover from a command that may inadvertenly make a radio go offline.
The idea is to launch a process in the background that sleeps for 5 minutes and then reboots the radio, so any changes not saved will be reverted. If the changes were successful, you’ll just need to log back in and kill the background process to keep the device from rebooting.
This can be helpful if your changing networking settings using ifconfig, trying to change routes, or something went wrong while trying to apply a system.cfg setting.
Commands
sleep 300 && reboot &
Execute whatever command you need to. i.e.
ifconfig 192.168.1.100
If your command worked you can log back into the device and search for the process id of the sleep command and kill it so the radio doesn’t reboot.
ps | grep sleep
Example output
2XC.v8.5.12# ps | grep sleep
412 admin 1636 S sleep 500
414 admin 1640 S grep sleep
2XC.v8.5.12#
Kill the pid
kill 412
Connect to Router over SSH
ssh admin@192.168.88.1
Check and install latest version of RouterOS. Will reboot the router. Need to hit Y to confirm upgrade.
system package update install
Upgrade routerboard firmware. Need to hit Y to confirm.
system routerboard upgrade
system reboot
Initiate a ssh connection to the server or device you want to use as a proxy. You can change the port to something else if so desired.
ssh username@ipaddress -D 1880
Log in and leave the session running
You can now setup your computer or browser to use the Proxy.
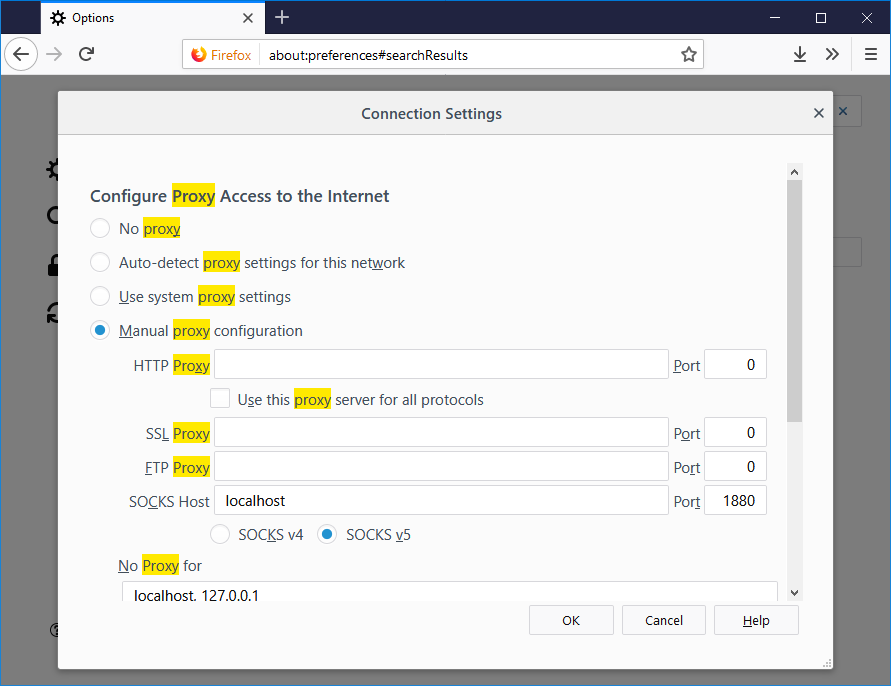
Specify SOCKS Host, hostname is either localhost or 127.0.0.1, the port is 1880.
Firefox example below.
Open your Oxidized config
vi .config/oxidized/config
Now edit your groups to include the following, part in bold is what specifies the SSH port. Note it needs to have the vars: line above it.
groups:
routeros:
username: admin
password: password
vars:
ssh_port: 2222
Save and quit with esc+:wq and run Oxidized
What we are going to do is create a proxy using ssh so we can tunnel our web traffic in Firefox through it.
First, launch putty and setup a SSH connection like you normally would.
Next, in Putty, go to the Connection, SSH, Tunnels. Set source port, change to Dynamic, and add. In this example we are using port 1880.
After you have it set, Open the connection and log in.
Now go to the Proxy settings in Firefox. You can open new tab, type about:preferences, hit enter, search proxy.
Set to Manual proxy configuration, then under SOCKS Host put localhost and the port number from Putty above, 1880 in our case.
 You should now be running over the proxy, can test by running a whats my ip address.
You should now be running over the proxy, can test by running a whats my ip address.
This can be particularly useful in cases where you need to access a local IP address range on something like a Ubiquiti radio or router. Or you need to check something from a different IP address.
Short version
List AirControl server(s)
mca-provision-list
Remove from AirControl Server
mca-provision-rm http://server-address
Expanded Steps
First you’ll need to SSH into your radio
Example:
ssh ubnt@192.168.1.20
Next run “mca-provision-list” to list the connection(s) the radio has, or is trying to connect to. If you have had the radio connected to multiple AirControl servers it will show more than one entry.
Example:
XM.v6.1.3# mca-provision-list unknown @ http://192.168.0.1:9081/AC2/report - XM.v6.1.3#
To remove, run “mca-provision-rm” with the AirControl address. You can simple use the “http://server-ip”, shouldn’t have to worry about the port number/AC2/report.
Example:
XM.v6.1.3# mca-provision-rm http://192.168.0.1 Found 1 entries matching 'http://192.168.0.1': Removing: unknown @ http://192.168.0.1:9081/AC2/report ... Found Backup1 on[1] ... Found Active on[2] ... Storing Active[1] ... [%100] Active->Backup[2] ... [%100] done. XM.v6.1.3#
The commands are for CentOS, but should work on Fedora and RedHat.
If semanage is not installed refer to here.
You would typically use this along with the systems firewall to allow a port through. Guide for firewalld and iptables. If you change it in the firewall and fail to add/edit it in semanage you can potentially get weird behavior like sshd not wanting to start after changing the port.
Add port
semanage port -a -t ssh_port_t -p tcp 2222
The above command allows the sshd service to start, using port 2222.
List allowed ports
semanage port -l
You can use grep to filter the results
Example:
[admin@localhost ~]# semanage port -l | grep ssh ssh_port_t tcp 2222, 22 [admin@localhost ~]#
Delete port
semanage port -d -p tcp 2222
Other examples
Allow SNMP
semanage port -a -t snmp_port_t -p udp 161
Setup SFTP Server
When finished you’ll have a SFTP server setup that is configured so the users are in a chroot environment, and can not ssh, or telnet to the server.
Install SSH server if it is not already
yum install openssh-server openssh-client
Create group that is limited to sftp so they can’t ssh, scp etc.
groupadd sftpusers
Add chroot settings to /etc/ssh/sshd_config. The %u is a variable, which is the users username.
Match Group sftpusers ChrootDirectory /sftp/%u ForceCommand internal-sftp
Make ftp directory
mkdir /sftp
Add SFTP user
useradd -g sftpusers -d /sftp -s /sbin/nologin newsftpuser
Create password for new user
passwd newsftpuser
Create directory for user
mkdir /sftp/newsftpuser
Create directory to put ftp files
mkdir /sftp/newsftpuser/files
Change permissions
chown newsftpuser:sftpusers /sftp/newsftpuser/files/
Restart sshd
systemctl restart sshd
Should be good to go. Test it by logging in with your favorite FTP client.
ssh: connect to host 192.168.1.158 port 22: Connection refused
Wrong SSH port. Check /etc/ssh/sshd_config on linux, or in RouterOS IP->services->SSH
ssh_exchange_identification: Connection closed by remote host
Check the hosts.allow and hosts.deny files. If your getting this error connecting to a Mikrotik check the IP services and the “Available From” addresses.