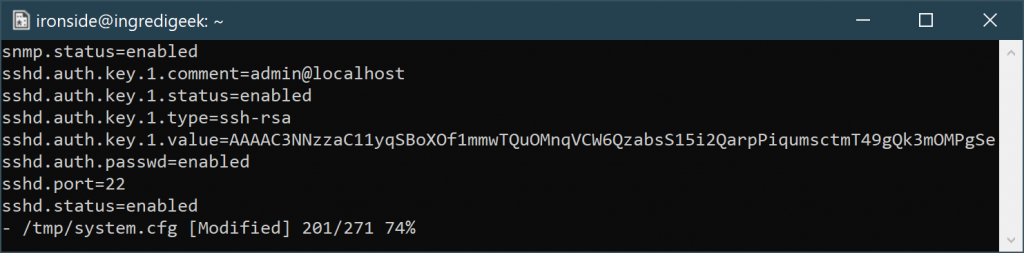
Who is this mcuser on ubiquiti devices? Nothing shows up in the radio config file about it, but the user shows up in /etc/passwd
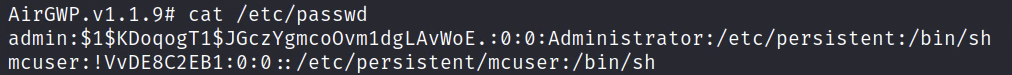
mcuser is used for AirControl2. If we look what is in the passwd file, we’ll notice that there is a ! at the beginning of the hash. Meaning that this password is disabled as the hash is not a proper hash. It’s only 10 characters long instead of the normal 13 for Unix DES hashes.
mcuser:!VvDE8C2EB1:0:0::/etc/persistent/mcuser:/bin/sh
https://community.ui.com/questions/Virus-atack-v2/be924ab6-5cb0-4f9b-a4f7-246025196cc0?page=10
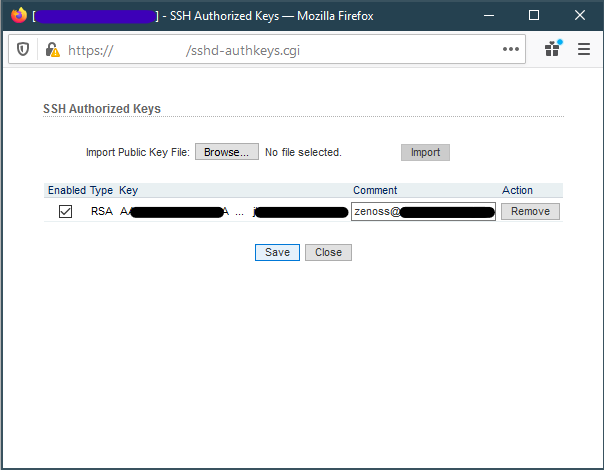
There is a valid ssh key, so the mcuser can ssh to the device without a password and do what it needs to do. Doing an ls on a device shows the following.
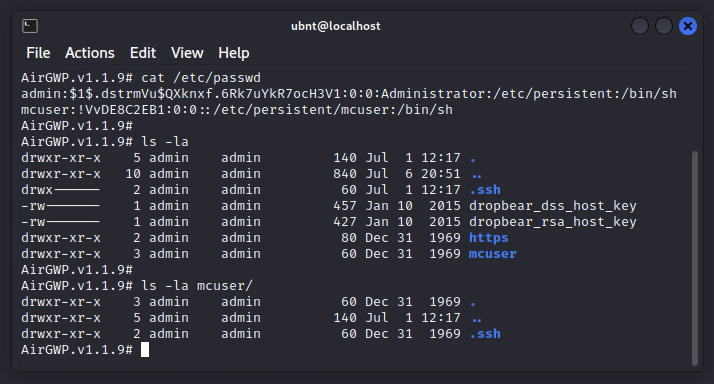
Refer to the following article on removing AirControl Provisioning