To check if SELinux is enabled or disabled, you can us the sestatus command
sestatus
Or you can grep what is in the SELinux config
cat /etc/selinux/config | grep SELINUX=.*abled

To check if SELinux is enabled or disabled, you can us the sestatus command
sestatus
Or you can grep what is in the SELinux config
cat /etc/selinux/config | grep SELINUX=.*abled
Install NTP
yum install ntp -y
Enable ntpd service
systemctl enable ntpd
Install qemu-img
dnf install qemu-img -y
Convert the image. Change vmimage to your image name.
qemu-img convert -f qcow2 -O vmdk vmimage.qcow2 vmimage.vmdkHad an issue that /run was randomly running out of space which in turn would interfere with the unifi-video service causing it to run, but not record.
/run looks like a tmpfs or ramdisk that Ubuntu sets up. So you can do a “temporary” fix by remounting the tmpfs with a larger size. Example below. If /run is a 2GB directory, you can remount changing the size from 2GB to 2.5GB.
sudo mount -t tmpsfs tmpfs /run -o remount,size=2500M
Note that it is a temporary fix and goes away after a reboot.
The issue ended up being that the WiFi UniFi controller was setup to auto backup everything once a week. So as it was backing stuff up, it would eat up the available space in the tmpfs, think there may be an issue with the size of the UniFi data and maybe not being able to fit it all in RAM?
Running the following command
df -h --max=1 /var | sort
shows the following
1.1M /run/udev 2.5G /run/ 2.5G /run/unifi <-- UniFi controller 4.0K /run/initramfs 8.0K /run/network 12K /run/user 288K /run/samba 404K /run/systemd
Looking inside the unifi directory shows the following folders. Looks like the they are temp files.
200M /run/unifi/ExpTmp351719567129045774 696M /run/unifi/ExpTmp3406220793759111216 1.6G /run/unifi/ExpTmp3368400690321364109 0 /run/unifi/work 2.5G /run/unifi
Running an ls inside the folder shows
-rw-r----- 1 unifi unifi 13971807 Jul 2 02:30 db.gz -rw-r----- 1 unifi unifi 1665223462 Jul 2 02:56 db_stat.gz
Looking inside the UniFi controller it is set to auto backup on Monday at 2:30AM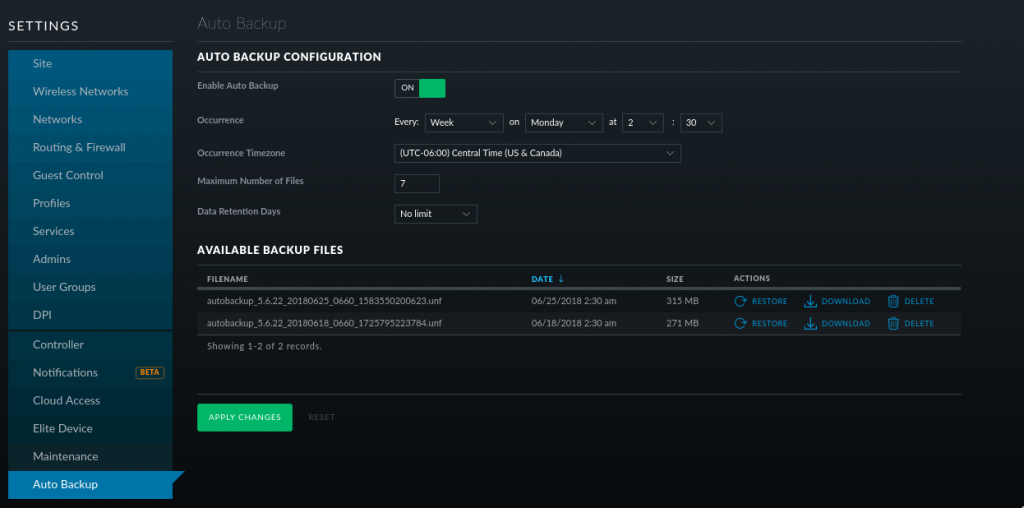
Looks like “/run/unifi” is used as a temporary folder to create the backups and when it is completed converts it to a .unf file and moves it to “/usr/lib/unifi/data/backup/autobackup/” So the left over temp files were never completed or something caused them to stop working. Maybe the backup was big enough to take up all the tmpfs space and cause the backup to fail.
Resolution. To fix the problem I turned the data retention down to a week and deleted the temp files in /var/unifi. Had to sudo su to root. sudo wasn’t cutting it for some reason.
sudo su rm -rf /var/unifi/Exp* exit
Should be all good now.
The reason is probably because the chrooted environment can’t resolve DNS.
Test it with
ping incredigeek.com
If it is not resolving, edit “/etc/resolv.conf” and change/add your nameserver. Or just replace everything in it with
echo "nameserver 4.2.2.2" > /etc/resolv.conf
It should now be able to resolve and you should be able to use yum, or dnf.
yum update
Typically your RAID volumes will show up as /dev/mdXXX
If it is not, it could be because the device mapper module is not loaded. Load it by running the following command.
modprobe dm-modAs a side note you can list the block devices using
dmraid -bhttps://bbs.archlinux.org/viewtopic.php?id=42321
If your still having trouble you can try installing mdadm and dmraid
apt-get install -y dmraid mdadm
Don’t know if this is the recommended way to delete a user, but it seems to work.
sudo service snmpd stop
Open up the snmpd.conf file in /var/lib and find the line with the SNMP user and delete the line
sudo vi /var/lib/snmp/snmpd.conf
The above file may be in the following location on RPM based systems.
sudo vi /var/lib/net-snmp/snmpd.conf
Save, exit, and start snmpd
sudo service snmpd start
These steps work for Ubuntu, but should work for any Debain based distro as well as CentOS, Fedora, RedHat etc.
Dig is a DNS lookup utility. It is included in most Linux distributions by default, but if it isn’t you can easily install dig with the following command.
The dig utility is apart of the dnsutils package
sudo apt-get install dnsutils -y
After it is installed, we can verify that it is working with
dig -v
For more information on how to use dig, refer to the following link.
https://www.howtogeek.com/663056/how-to-use-the-dig-command-on-linux/
The following is copied and pasted from the dig man page.
NAME
dig - DNS lookup utility
SYNOPSIS
dig [@server] [-b address] [-c class] [-f filename] [-k filename] [-m] [-p port#] [-q name]
[-t type] [-v] [-x addr] [-y [hmac:]name:key] [[-4] | [-6]] [name] [type] [class]
[queryopt...]
dig [-h]
dig [global-queryopt...] [query...]
DESCRIPTION
dig is a flexible tool for interrogating DNS name servers. It performs DNS lookups and
displays the answers that are returned from the name server(s) that were queried. Most DNS
administrators use dig to troubleshoot DNS problems because of its flexibility, ease of use
and clarity of output. Other lookup tools tend to have less functionality than dig.
Although dig is normally used with command-line arguments, it also has a batch mode of
operation for reading lookup requests from a file. A brief summary of its command-line
arguments and options is printed when the -h option is given. Unlike earlier versions, the
BIND 9 implementation of dig allows multiple lookups to be issued from the command line.
Unless it is told to query a specific name server, dig will try each of the servers listed
in /etc/resolv.conf. If no usable server addresses are found, dig will send the query to the
local host.
When no command line arguments or options are given, dig will perform an NS query for "."
(the root).
It is possible to set per-user defaults for dig via ${HOME}/.digrc. This file is read and
any options in it are applied before the command line arguments. The -r option disables this
feature, for scripts that need predictable behaviour.
The IN and CH class names overlap with the IN and CH top level domain names. Either use the
-t and -c options to specify the type and class, use the -q the specify the domain name, or
use "IN." and "CH." when looking up these top level domains.
SIMPLE USAGE
A typical invocation of dig looks like:
dig @server name type
where:
server
is the name or IP address of the name server to query. This can be an IPv4 address in
dotted-decimal notation or an IPv6 address in colon-delimited notation. When the
supplied server argument is a hostname, dig resolves that name before querying that name
server.
If no server argument is provided, dig consults /etc/resolv.conf; if an address is found
there, it queries the name server at that address. If either of the -4 or -6 options are
in use, then only addresses for the corresponding transport will be tried. If no usable
addresses are found, dig will send the query to the local host. The reply from the name
server that responds is displayed.
name
is the name of the resource record that is to be looked up.
type
indicates what type of query is required — ANY, A, MX, SIG, etc. type can be any valid
query type. If no type argument is supplied, dig will perform a lookup for an A record.
Copy and paste the following into a file named mtbypass.sh and then “chmod +x mtbypass.sh” Or download from this direct link. Be sure to change the username and password
#!bin/bash
filelist="bypasslist.txt"
username="admin"
password="password!"
ip="$1"
for i in `cat ${filelist}`
do
address=`echo $i | cut -d= -f1`
mac=`echo $i | cut -d= -f2`
sshpass -p ${password} ssh ${username}@${ip} "ip hotspot ip-binding add address=${address} mac-address=${mac} type=bypassed"
done
Now create a file named bypasslist.txt and put all the addresses you want bypassed. You’ll need the Mac Address and the IP Address.
Example file
192.168.88.2=4C:5E:0C:B8:4E:01 192.168.88.3=3E:AA:A1:2D:8B:2C 192.168.88.5=DE:D1:39:65:91:4E
Usage of script is
./mtbypass.sh MikrotikIP
Example:
./mtbypass.sh 192.168.88.1
List enabled system services
systemctl list-unit-files | grep enabled
Can also grep by disabled
systemctl list-unit-files | grep disabled
Or look for a specific service
systemctl list-unit-files | grep -i service-name