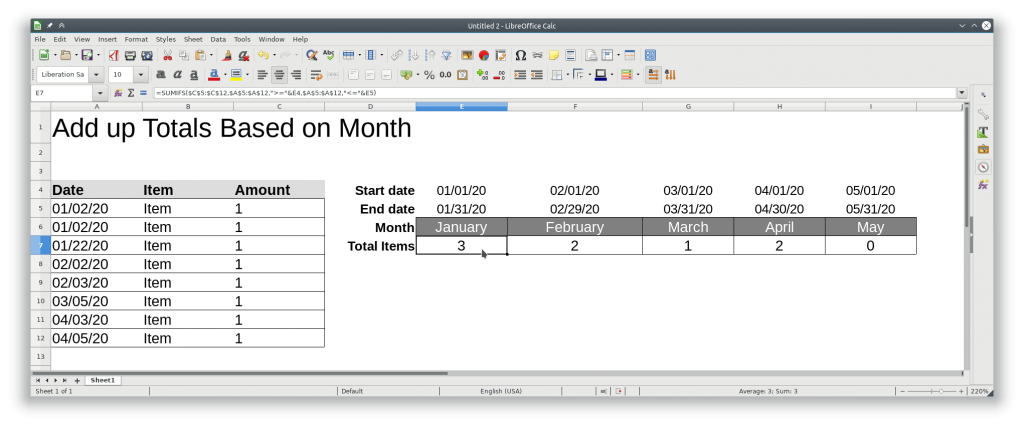
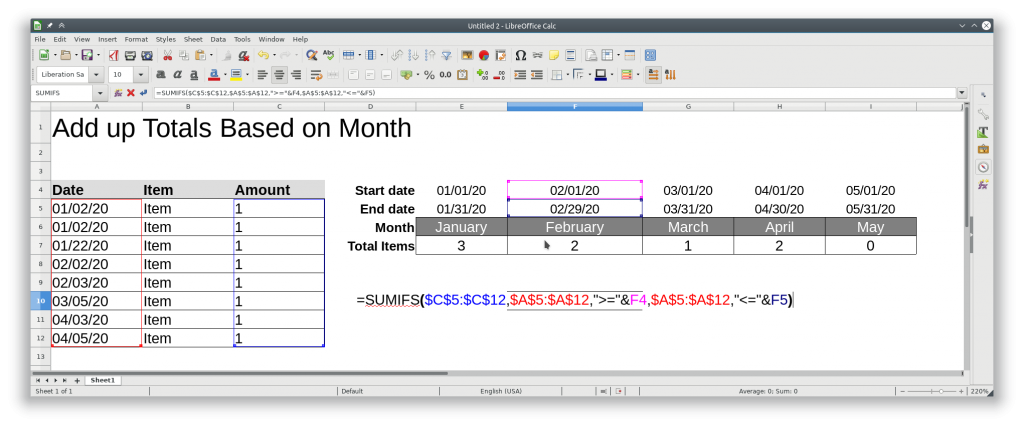
All the following commands are run from the “/opt/librenms” directory
$ sudo ./daily.sh
Re-running /opt/librenms/daily.sh as librenms user
Updating to latest codebase FAIL
error: Your local changes to the following files would be overwritten by merge:
html/js/lang/de.js
html/js/lang/en.js
Please, commit your changes or stash them before you can merge.
...
$
Checking with validate.php shows that you can run githup-remove to fix it
$ sudo ./validate.php
[WARN] Your install is over 24 hours out of date, last update: Mon, 23 Feb 2020 05:43:12 +0000
[FIX]:
Make sure your daily.sh cron is running and run ./daily.sh by hand to see if there are any errors.
[WARN] Your local git contains modified files, this could prevent automatic updates.
[FIX]:
You can fix this with ./scripts/github-remove
Modified Files:
html/js/lang/de.js
...
$
Run “sudo ./scripts/github-remove -d”
$ sudo ./scripts/github-remove -d
Are you sure you want to delete all modified and untracked files? [y/N] y
$
You should also be able to remove the files individually if the above command does not work.
Run validate again to make sure it checks out good.
Now run ./daily.sh