You can add the following in the ansible config file in “inventory/host_vars/matrix.yourdomain.com/vars.yml” to use a self signed certificate. Only recommended for testing purposes.
matrix_ssl_retrieval_method: self-signed

You can add the following in the ansible config file in “inventory/host_vars/matrix.yourdomain.com/vars.yml” to use a self signed certificate. Only recommended for testing purposes.
matrix_ssl_retrieval_method: self-signed
ansible-playbook -i inventory/hosts setup.yml --tags=setup-system-user --ask-become-pass
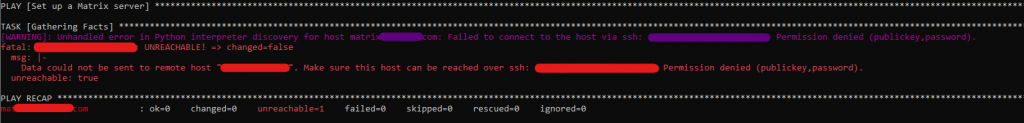
Looks like the above issue is that Ansible is not able to authenticate with the server. By default it looks to try and use ssh keys, but I don’t have any passwordless ssh keys set up for Ansible to use so it fails while attempting to connect. The work around it to make sure you have sshpass installed and then specify –ask-pass to the end of the command.
ansible-playbook -i inventory/hosts setup.yml --tags=setup-system-user --ask-become-pass --ask-pass
When the command runs it’ll ask you for the ssh password and then use that.
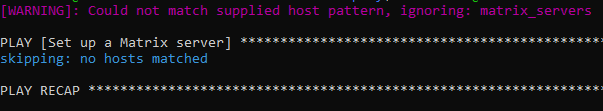
If you get the above error when you try running
ansible-playbook -i inventory/hosts setup.yml --tags=setup-system-user
Check and verify that you have [matrix_servers] in your inventory/hosts file
That file should contain the following.
[matrix_servers] matrix. ansible_host= ansible_ssh_user=root
This is part of a series of posts on backing up and restoring a backup for Matrix Synapse server. Synapse was installed using the matrix-docker-ansible deployment which while a little complicated can greatly ease management later on down the road. All the main components are in docker containers so we need to use docker to access.
As the root user run
docker exec --env-file=/matrix/postgres/env-postgres-psql matrix-postgres pg_dumpall -h matrix-postgres | gzip -c > /matrix/postgres.sql.gz
This will dump the Postgres database in /matrix/postgres.sql.gz
We can use this later to restore to a new server or keep as a backup.
rsnapshot is a utility that uses rsync to backup files locally or it can backup files from a remote server.
While trying to figure out a good solution for backing up an Ubuntu Server I decided to try rsnapshot, however since it can either create a local backup or pull a remote backup it needs to be configured to do that on the backup server side. It does not “push” a backup to a backup server.
Some helpful snippits from the man file.
rsnapshot will typically be invoked as root by a cron job, or series of cron jobs. It is possible, however, to run as any arbitrary user with an alternate configuration file.... USAGE rsnapshot can be used by any user, but for system-wide backups you will probably want to run it as root. ... NOTES Make sure your /etc/rsnapshot.conf file has all elements separated by tabs. See /usr/share/doc/rsnapshot/examples/rsnapshot.conf.default.gz for a working example file.Make sure you put a trailing slash on the end of all directory references. If you don't, you may have extra directories created in your snapshots. For more information on how the trailing slash is handled, see the rsync(1) manpage.
Scenario
Host A runs xyz application and host B is the backup server. We create a backup user on host A, host B then uses that user to ssh and rsync backups to itself.
The following commands are fairly straight forward. Change backupuser to whatever you want to call your backup user.
sudo useradd -m backupuser passwd backupuser sudo usermod -a -G sudo backupuser
We need to setup the backup user to be able to use “sudo rsync” without having to input the user password. If we don’t use sudo we can’t access system files for backups. And if we have to manually input the password every time rsync runs, then the backups would not be automatic. The following link was helpful.
https://unix.stackexchange.com/questions/325100/proper-way-to-set-up-rsnapshot-over-ssh
All we need to do is create a file in /etc/sudoers.d/username and then tell it we don’t need to enter a password when “sudo rsync” is run.
sudo tee /etc/sudoers.d/backupuser <<<'backupuser ALL = (root) NOPASSWD: /usr/bin/rsync'Log into the backup server
Create SSH keys. Note that since rsnapshot wants to run as root, we create the key and copy it as the root user.
sudo ssh-keygen
Accept all the defaults so we can login from the backup server without having to enter in a password.
Copy ssh key to the server we are wanting to back up
sudo ssh-copy-id backupuser@ip
enter in the password and the the key should get copied it over. Once complete, verify that you can login without having to enter in a password.
Open up the rsnapshot config file and modify where appropriate. /etc/rsnapshot.conf
Change the path to where the snapshots are stored. By default it stores them under /.snapshots. I moved it under a local user as I am not needing to use rsnapshot to backup the local backup server files.
# SNAPSHOT ROOT DIRECTORY
snapshot_root /home/user/rsnapshot/snapshots/
Add a daily backup option under Backup levels
# BACKUP LEVELS / INTERVAL #
retain daily 6
Setup remote server to get a backup from. Replace ipaddress and directories as needed. hostname is the sever name. You can change to whatever you want.
### BACKUP POINTS / SCRIPTS ### # LOCALHOST # Comment or delete entries unless you want to backup those as well # EXAMPLE.COM backup backupuser@ipaddress:/home/ hostname/ +rsync_long_args=--rsync-path="sudo rsync"
If you would like to back up multiple locations you can create multiple entries with different remote paths. Example locations to add
backup backupuser@ipaddress:/etc/ hostname/ +rsync_long_args=--rsync-path="sudo rsync" backup backupuser@ipaddress:/usr/local/ hostname/ +rsync_long_args=--rsync-path="sudo rsync"
Verify that the config is good with
sudo rsnapshot configtest
It should return Syntax OK
sudo crontab -e
Add the following line to run rsnapshot at 3AM every day. More information about crontab can be found here.
0 3 * * * /usr/bin/rsnapshot daily
Manually run a backup to verify everything is set up correctly.
sudo rsnapshot daily
After it runs you can check the directory you specified in the config file to verify that the files did get copied.
Nvidia GTX 1070 ETH Hashrate and Power Consumption
The following is the estimated Hashrate and power consumption of a GTX 1070 based on web sources.
Cost Used (eBay)
February 2021: $300 – $500
Hashrate: 26/Mhs
Power Consumption
Average: 130 W
Average Mhs Per Watt : 0.2/Mhs
Average Watts Per Mhs: 5 W
Profitability is about $2.97/day as of February 9, 2021
https://whattomine.com/coins/151-eth-ethash?hr=26&p=130&fee=0.0&cost=0.1&hcost=0.0&commit=Calculate
Nvidia GTX 1070 ETH Hashrate and Power Consumption
The following is the estimated Hashrate and power consumption of a GTX 1070 based on web sources.
Cost Used (eBay)
February 2021: $300 – $500
Hashrate: 26/Mhs
Power Consumption
Average: 130 W
Average Mhs Per Watt : 0.2/Mhs
Average Watts Per Mhs: 5 W
Profitability is about $2.97/day as of February 9, 2021
https://whattomine.com/coins/151-eth-ethash?hr=26&p=130&fee=0.0&cost=0.1&hcost=0.0&commit=Calculate
Nvidia RTX 3080 ETH Hashrate and Power Consumption
The following is the estimated Hashrate and power consumption of a RTX 3080 based on web sources.
Cost Used (eBay)
February 2021: $1600 – $2000
Hashrate: 97/Mhs
Power Consumption
Average: 250 W
Average Mhs Per Watt : 0.39/Mhs
Average Watts Per Mhs: 2.58 W
Profitability is about $12.45/day as of February 9, 2021
Nvidia RTX 3070 ETH Hashrate and Power Consumption
The following is the estimated Hashrate and power consumption of a RTX 3070 based on web sources.
It seems that the hashrate and power consumption is basically the same as an RTX 3060 Ti
Cost Used (eBay)
February 2021: $950 – $1000
Hashrate: 62/Mhs
Power Consumption
Average: 122 W
Average Mhs Per Watt : 0.51/Mhs
Average Watts Per Mhs: 1.97 W
Profitability is about $8.39/day as of February 9, 2021
https://whattomine.com/coins/151-eth-ethash?hr=62&p=122&fee=0.0&cost=0.1&hcost=0.0&commit=Calculate
Nvidia RTX 3060 Ti ETH Hashrate and Power Consumption
The following is the estimated Hashrate and power consumption of a RTX 3060 Ti based on web sources.
Cost Used (eBay)
February 2021: $900 – $1000
Hashrate: 60/Mhs
Power Consumption
Average: 120 W
Average Mhs Per Watt : 0.5/Mhs
Average Watts Per Mhs: 2 W
Profitability is about $7.70/day as of February 9, 2021