Basic steps are
- Change password with passwd
- Copy passwd hash to /tmp/system.cfg
- Apply Changes
Changing Password with passwd
The passwd command is normally used for changing the password for a Linux user. We’ll use it to change our user password and then copy the hash out of the /etc/passwd file to use in the Ubiquiti config file.
UVC.v4.18.37.67# passwd
Changing password for admin
New password:
Retype password:
passwd: password for admin changed by admin
UVC.v4.18.37.67#
Copy passwd hash to /tmp/system.cfg
Using “cat /etc/passwd”, we can get what the new password hash is and can copy that into the /tmp/system.cfg file.
UVC.v4.18.37.67# cat /etc/passwd
admin:$6$K4VfN1jGcxaX63Eo$yMGBg7jgCCg.HorkmkQf9wnQcEko.1onZcAa6ua421LonYgfYr8FgHprrwkMqaTYzH0KqCtOEPqDlB3AvkvcW.:0:0:Administrator:/etc/persistent:/bin/sh
UVC.v4.18.37.67#
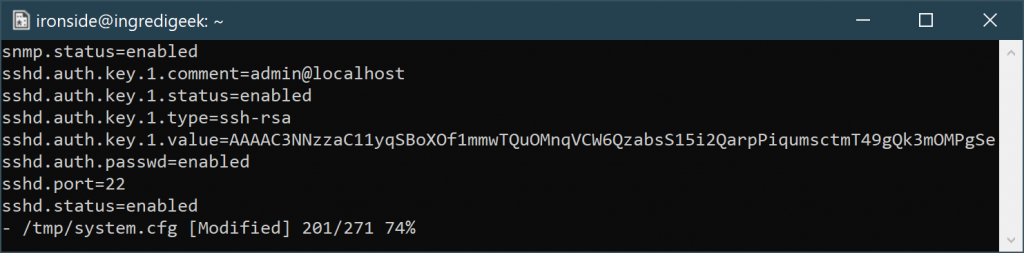
Open up the /tmp/system.cfg config file, find the section below and replace the hash part, i.e. the part that is in bold.
users.1.name=admin
users.1.password=$6$K4VfN1jGcxaX63Eo$yMGBg7jgCCg.HorkmkQf9wnQcEko.1onZcAa6ua421LonYgfYr8FgHprrwkMqaTYzH0KqCtOEPqDlB3AvkvcW.
users.1.status=1
As a side note, you can copy and past all of the “users.1.*” lines and change the 1 to 2 and have a second user.
Apply Changes
You can use the following command to write the changes and then reboot the camera.
cfgmtd -f /tmp/system.cfg -w && reboot
Long Example
[admin@localhost ~]$ ssh ubnt@10.96.1.91
ubnt@10.96.1.91's password:
BusyBox v1.29.2 () built-in shell (ash)
UVC.v4.18.37.67# passwd
Changing password for admin
New password:
Retype password:
passwd: password for admin changed by admin
UVC.v4.18.37.67# cat /etc/passwd
admin:$6$K4VfN1jGcxaX63Eo$yMGBg7jgCCg.HorkmkQf9wnQcEko.1onZcAa6ua421LonYgfYr8FgHprrwkMqaTYzH0KqCtOEPqDlB3AvkvcW.:0:0:Administrator:/etc/persistent:/bin/sh
UVC.v4.18.37.67# vi /tmp/system.cfg <- Edit the text file and replace the hash with the one from above
UVC.v4.18.37.67# cfgmtd -f /tmp/system.cfg -w && reboot