It can be common for older devices to throw errors like the following when trying to ssh into them.
Unable to negotiate with 192.168.1.1 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
or
Unable to negotiate with 192.168.1.1 port 22: no matching host key type found. Their offer: ssh-rsa
There can also be a No Matching Cipher Found error. We have talked about that in the past.
The issue is that your version of SSH does not support those older, and most likely insecure, Key Exchange and Host Key algorithms types. The errors do give us enough info to add the right options to connect to the device.
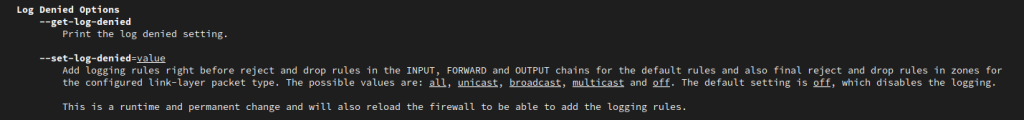
No Matching Key Exchange Method Found
For the “no matching key exchange method found.” we need to manually add the KexAlgorithms option. KexAlgorithms means Key Exchange Algorithm.
ssh -o KexAlgorithms=+diffie-hellman-group14-sha1 username@192.168.1.1
Change out “diffie-hellman-group14-sha1” for a supported Key Exchange algorithm.
No Matching Host Key Type Found
This issue is with the Host Key algorithm type. We’ll use the -o option with the HostKeyAlgorithms option.
ssh -o HostKeyAlgorithms=+ssh-rsa admin@192.168.1.1
Change our ssh-rsa with a supported “Their offer:” Host Key.
Putting it all together
You can combine the options if needed.
ssh -o KexAlgorithms=+diffie-hellman-group14-sha1 -o HostKeyAlgorithms=+ssh-rsa admin@192.168.1.1
We have covered some of these topics before. Be sure to check them out.
no matching cipher found. Their offer: aes128-cbc,3des-cbc…
no matching key exchange method found. Their offer: diffie-hellman-group1-sha1